A brand new report from cloud safety firm Zscaler sheds gentle on the rising cell threats on Android working techniques, in addition to IoT and OT gadgets threats. The findings come as greater than 60% of the worldwide Web site visitors is now generated by cell gadgets and financially-oriented cell threats have grown by 111% over the past yr.
A listing of cell malware threats
Zscaler’s ThreatLabz witnessed a 29% rise in banking cell malware over the earlier yr, with banking malware representing 20% of the overall Android risk panorama.
Most lively banking malware households to this point embody:
- Vultur, which is primarily distributed via the Google Play Retailer.
- Hydra, distributed by way of phishing messages, web sites, and malicious Google Play Retailer purposes.
- Ermac, designed to steal monetary information from banking and pockets apps.
- Anatsa, also called TeaBot
- Coper, also called Octo
- Nexus, primarily targets cryptocurrency accounts
Most of those banking malware file keystrokes, hijack credentials, and intercept SMS messages with the intention to bypass Multi-Issue Authentication.
SEE: How one can Create an Efficient Cybersecurity Consciousness Program (TechRepublic Premium)
Adware threats soar by greater than 100%
Along with banking malware, spyware and adware threats have additionally grown, with researchers indicating that blocked transactions elevated by 100% over the earlier yr.
Probably the most prevalent spyware and adware reported are SpyLoan, SpinOk, and SpyNote.
- SpyLoan has the power to steal private information from gadgets, corresponding to accounts, gadget info, name logs, put in apps, calendar occasions, metadata, and extra.
- SpinOk spyware and adware collects delicate information and recordsdata from varied places on the contaminated gadget and exfiltrates the information to an attacker-controlled server.
- SpyNote, also called CypherRat, gives extra distant entry capabilities in order that the attacker can management execution of software program on the cell gadget.
Based on Zscaler, most cell malware focused India (28%), the U.S. (27%), and Canada (15%), adopted by South Africa (6%), The Netherlands (5%), Mexico (4%), Nigeria (3%), Brazil (3%), Singapore (3%) and the Philippines (2%).
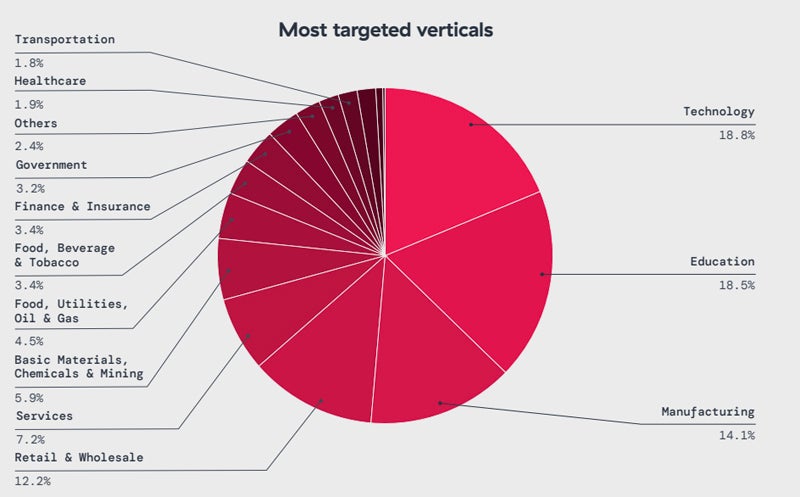
Impacted sectors embody expertise (18%), training (18%), manufacturing (14%), retail and wholesale (12%), and companies (7%).
Cellular malware are distributed by way of varied strategies. One methodology consists of utilizing social engineering methods. For instance, Zscaler experiences that attackers deployed the Copybara cell malware through the use of voice phishing (vishing) assaults, the place the sufferer acquired voice directions to put in the malware on their Android telephones.
QR code rip-off can also be widespread, the place victims are tricked into scanning malicious QR codes resulting in malware infections or, in some instances, to phishing pages.
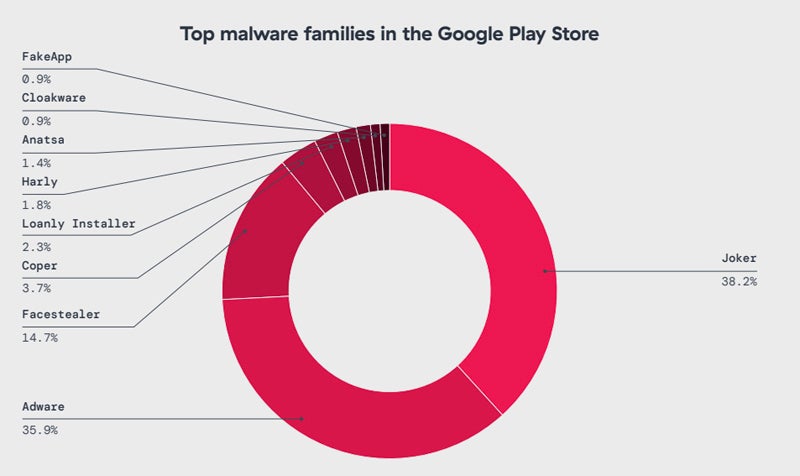
Some malware can also be accessible on the Google Play Retailer. This consists of Joker — which silently subscribes customers to premium companies with out their consent to generate costs — adopted by adware malware sort and facestealer, a Fb account stealer.
Total, regardless of an general lower in Android assaults, financially-oriented cell threats have grown by 111% over the past yr.
IoT and OT threats
Web of Issues and Operational Know-how environments maintain increasing and are more and more focused by attackers, based on the report. The researchers point out that the variety of IoT gadgets interacting with them has grown by 37% year-over-year.
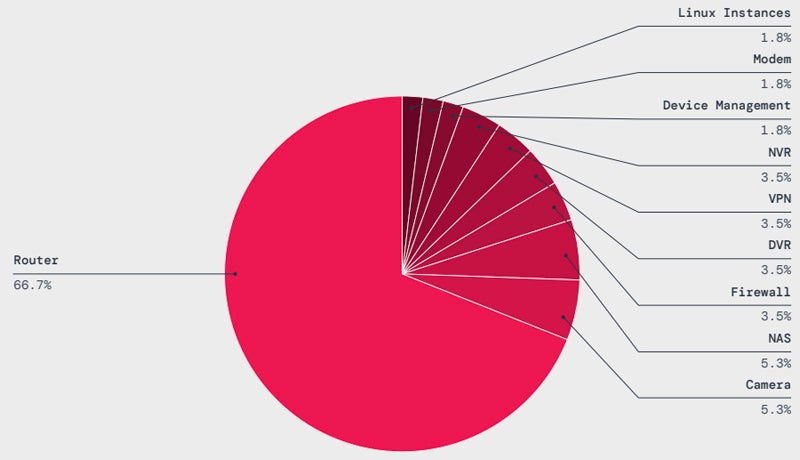
IoT malware assaults have grown by 45% over the previous yr, with routers being probably the most focused sort of gadget, with greater than 66% of assaults aimed toward these gadgets. The main malware households hitting IoT gadgets are Mirai (36.3%) and Gafgyt (21.2%). Botnets constructed with these malware on IoT gadgets can be utilized to launch massive Distributed Denial of Service assaults.
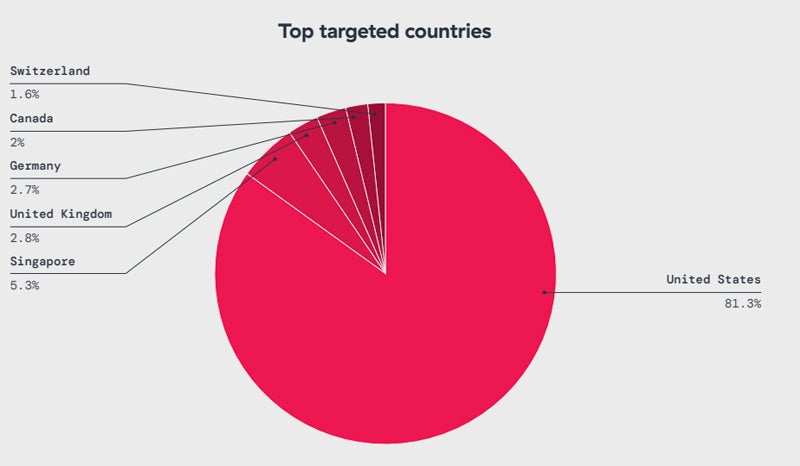
Concerning the geographical distribution, greater than 81% of IoT malware assaults are aimed on the U.S., adopted by Singapore (5.3%), the UK (2.8%), Germany (2.7%), Canada (2%), and Switzerland (1.6%).
High sectors impacted by IoT malware assaults are manufacturing (36.9%), transportation (14.2%), meals, beverage, and tobacco (11.1%).
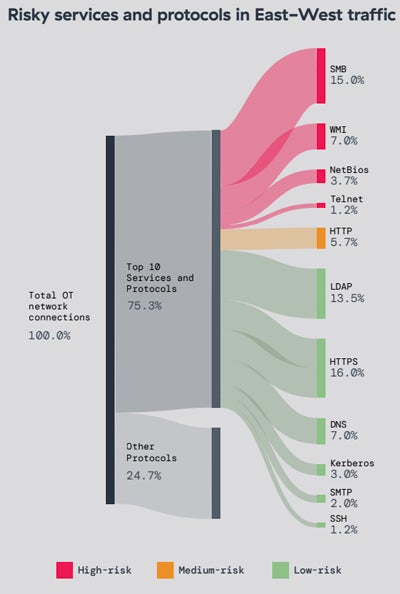
On the OT aspect, 50% of the gadgets in lots of deployments use legacy, end-of-life working techniques. Protocols susceptible to totally different vulnerabilities are additionally usually uncovered in OT environments, corresponding to SMB or WMI.
For instance, ThreatLabz analyzed the OT content material of a large-scale manufacturing group, comprising greater than 17,000 linked OT gadgets throughout greater than 40 totally different places. Every website contained greater than 500 OT gadgets with end-of-life Microsoft Home windows working techniques, lots of which had recognized vulnerabilities.
67% of the worldwide site visitors to the OT gadgets was unauthorized or blocked.
What’s going to the longer term appear like?
Based on Zscaler, IoT and OT gadgets will stay major risk vectors, whereas the manufacturing sector will stay a prime goal for IoT assaults, together with ransomware.
Zscaler additionally suspects synthetic intelligence might be more and more used to ship high-quality phishing campaigns concentrating on cell customers. Nevertheless, AI can even assist defenders automate vital capabilities and higher prioritize their efforts.
How one can defend IoT and OT gadgets from cyber assaults
To guard from threats on IoT and OT gadgets, it’s essential to:
- Achieve visibility on IoT and OT gadgets is a precedence. Organizations want to find, classify, and keep lists of all IoT and OT gadgets used of their full surroundings.
- Maintain all techniques and software program updated and patched to stop being compromised by widespread vulnerabilities.
- Community logs have to be collected and analyzed. Suspicious consumer account entry and system occasions have to be significantly monitored.
- Multi-factor authentication have to be deployed when potential, and default passwords and accounts have to be modified or disabled.
- Zero-Belief gadget segmentation ought to be enforced for IoT and OT belongings to reduce information publicity.
How one can defend cell gadgets from cyber assaults
To guard from threats on cell gadgets, you will need to:
- Set up safety purposes on the gadgets, to guard them from malware and potential phishing makes an attempt.
- Any hyperlink arriving on the cell phone, irrespective of the applying, ought to be cautiously examined. In case of suspicious hyperlink, it should not be clicked and reported to IT safety workers.
- Unknown purposes have to be averted. Additionally, purposes ought to by no means be downloaded from third events or untrusted sources.
Firms must also be cautious of purposes requesting updates instantly after set up. An software downloaded from the Play Retailer ought to be the most recent model. If an app requests permission to replace instantly after set up, it ought to be handled as suspicious and will point out malware trying to obtain extra malicious parts.
Disclosure: I work for Development Micro, however the views expressed on this article are mine.